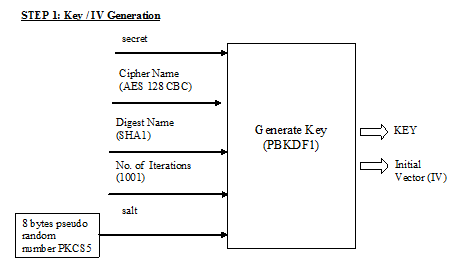
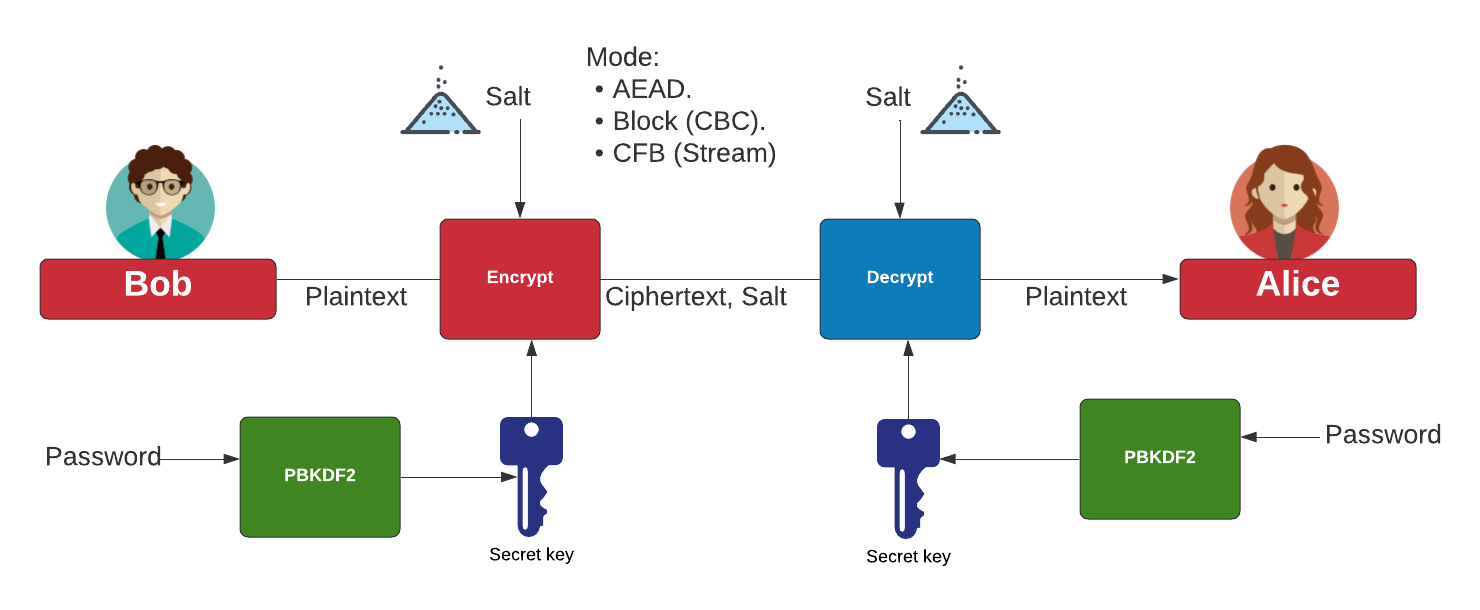
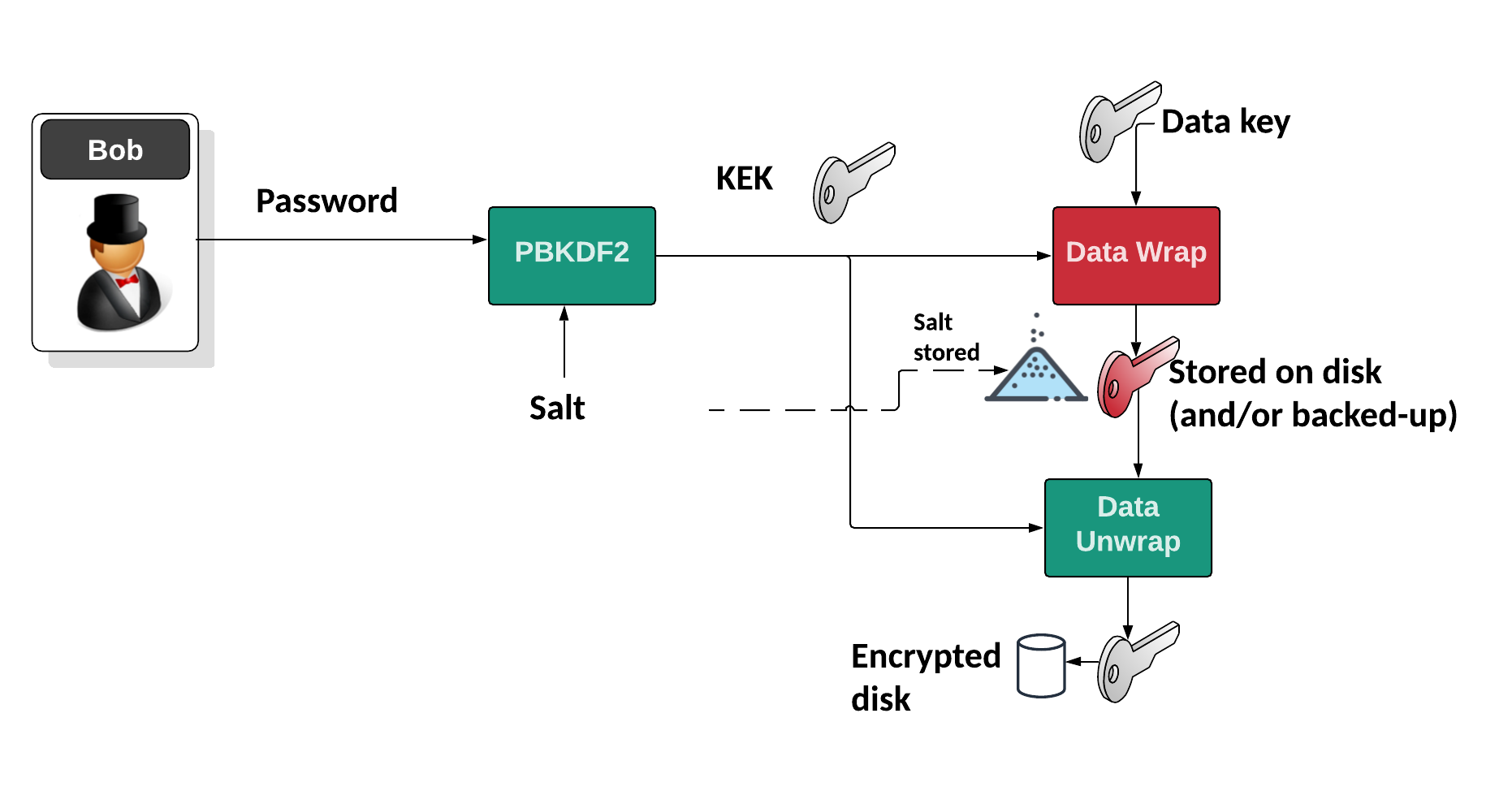
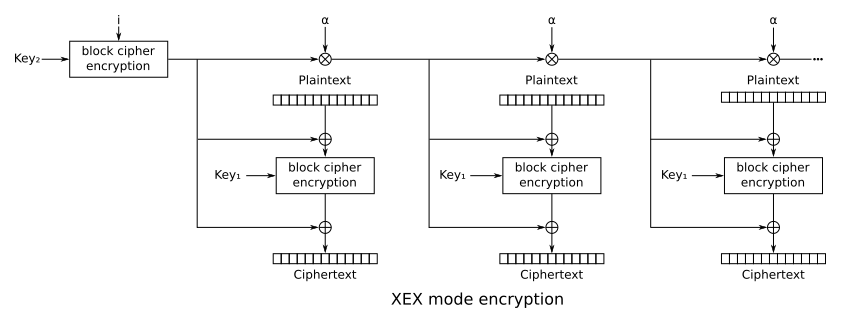
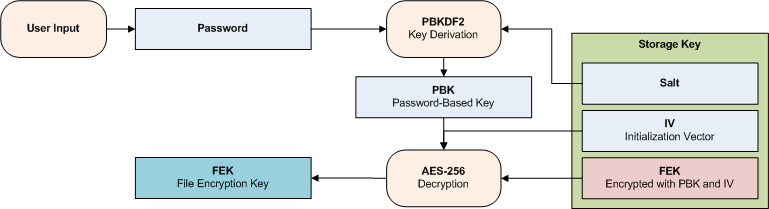
CISSP PRACTICE QUESTIONS – 20200713 by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu
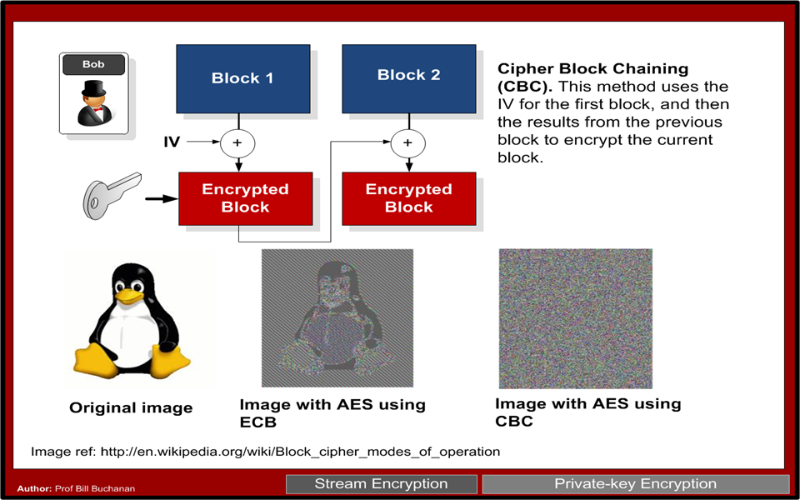
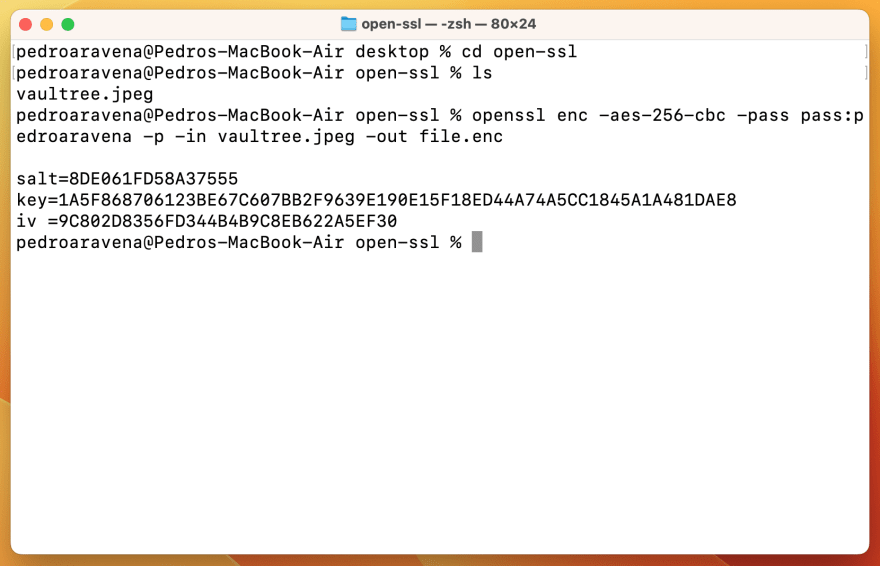
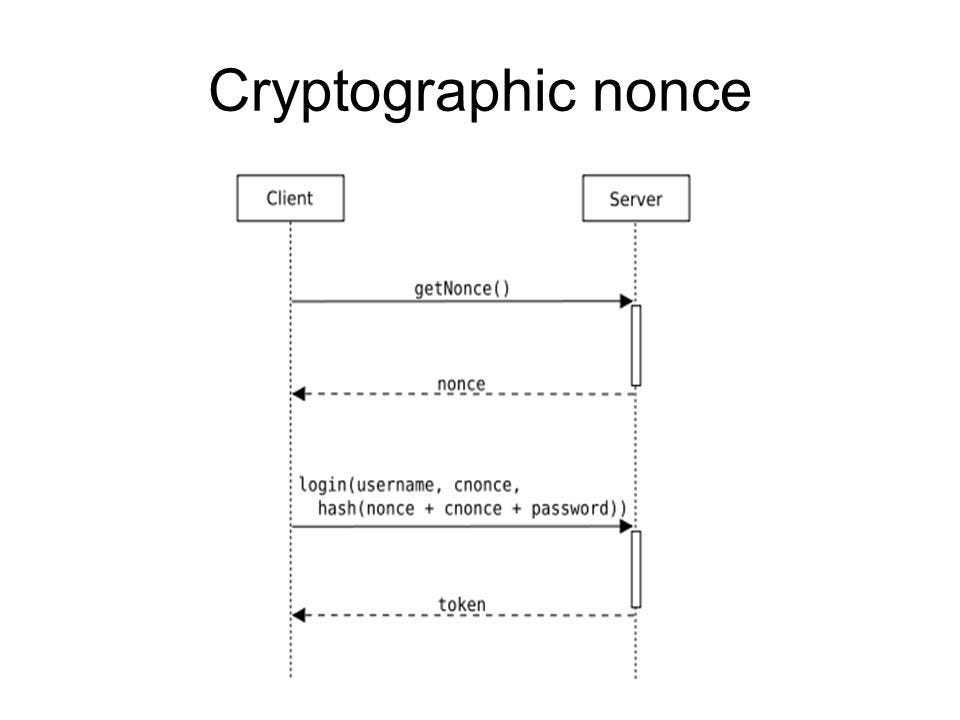
initialization vector - What is the main difference between a key, an IV and a nonce? - Cryptography Stack Exchange

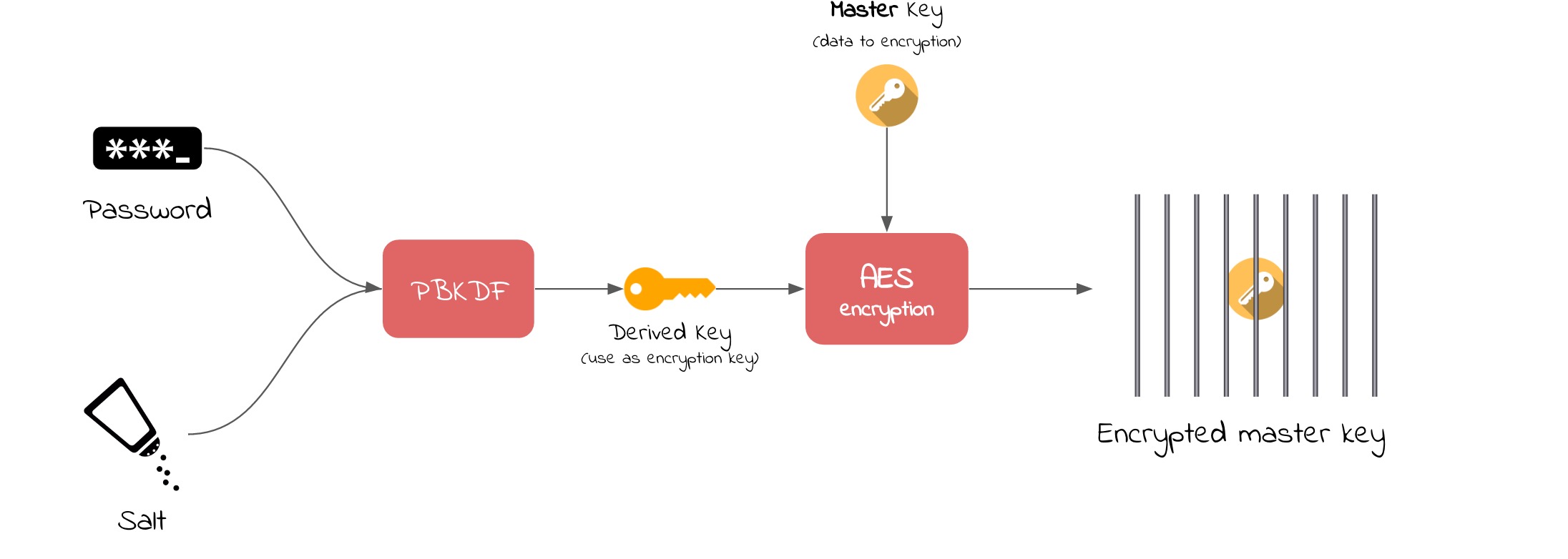
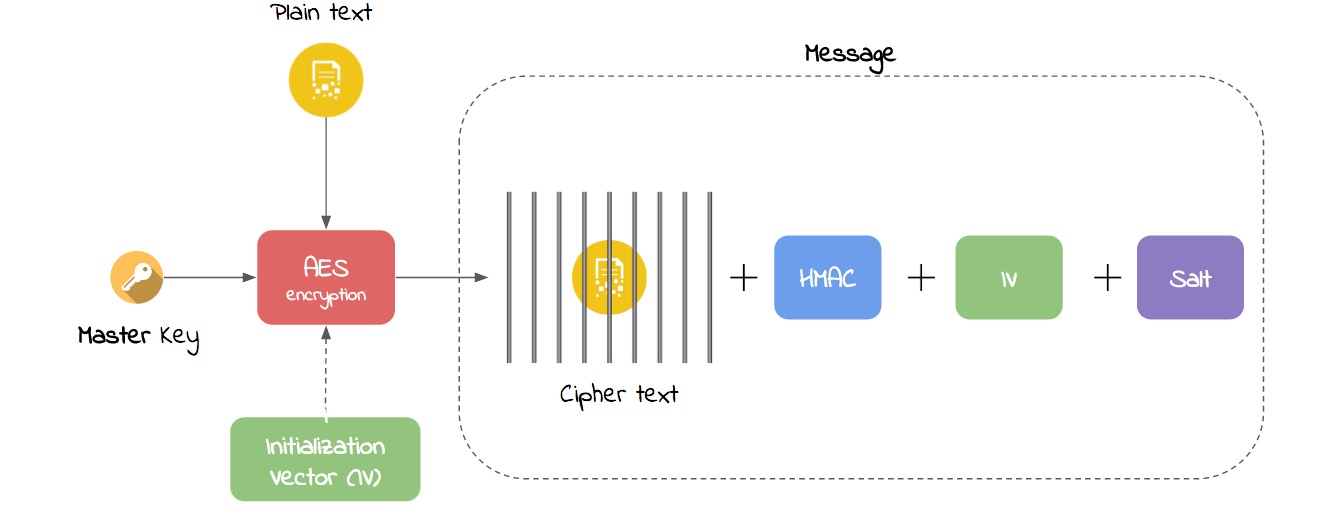
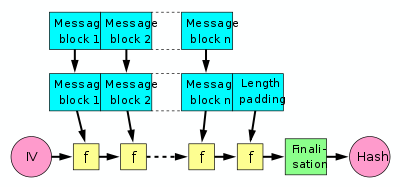
If you copied any of these popular StackOverflow encryption code snippets, then you coded it wrong – Little Man In My Head